Can Self-Sovereign Identity (SSI) provide you with control over your digital identity: a techno-legal analysis of opportunities and challenges
The SSI expands the existing identity theories, and claims that we need to redefine our identity. Most SSI projects build their infrastructures on blockchain networks. For the curious, two previous blogposts on SSI made a conceptual analysis based on SSI principles and assessed the conceptual alignment of the SSI with the GDPR. It was established that the same words are used to refer different meanings, which might be deceiving for a user that has no technical expertise on the issue. One overarching principle, among others, analyzed in the previous blogposts was control. This blogpost goes deeper into this principle of SSI, asking whether they might be achieved, considering the most common technical aspects of the SSI ecosystem, i.e., wallets, Verifiable Credentials (VC) ecosystem, including Decentralized Identifiers (DIDs). As we go through these components, a brief overview of a reality check is provided based on the considerations regarding their ability to provide control and protection to data subjects.
Essentials of the SSI management system
To examine the data protection implications of using SSI we need first to look into the basics of these systems. This is not an easy task as there are already more than hundreds of SSI projects using various techniques. However, the basic components, e.g., wallets, remain more or less the same. For the purpose of this blogpost, I chose the most mature specifications and models, i.e., W3C DID Core 1.0, and Verifiable Credentials Data Model v1.1.

Your key is in others’ wallets
Most online interactions base their security on Public Key Infrastructures. Basically, it is an asymmetric cryptography setup consisting of the software, hardware, procedures, and policies required to manage public and private keys. Traditional PKI’s are handled by centralized trusted parties, e.g., certificate authorities or message service providers. These intermediaries (trusted third parties) issue, sign and store digital certificates that certifies the ownership of a public key. Such parties either manage private keys within their servers or they outsource the secure management. In other words, third parties control your private keys. The structure is susceptible to vulnerabilities such as being a single point of failure where, for example if the signing keys of the authority is leaked, the whole PKI is compromised. In such scenarios, as in the Stuxnet attack, fraudulent certificates might be issued. What happens next is likely to be compromised credentials, identity theft and resale of the credentials on the Dark Web.
SSI keeps your keys in your wallets
Blockchain based SSI management projects claim that they remove intermediaries such as certificate authorities and provide the individuals with the full control over private keys so that there is no control over keys and no access to the credentials of everyone using the system accessed by a third party. The control promise bases its argument on self-certification and self-administration of the keys.
In addition to these, self-managed storage (wallets) of identity data is used to provide a control feeling to the user, based on visualization of data and management interfaces with the rest of the SSI community. Wallets are software that allow data subjects to manage their private key, store DIDs and VC. Although still being developed, some companies offer wallets that are ready to be downloaded.
A deeper look into the SSI wallet: DIDs
Decentralized identifiers are globally unique and persistent Uniform Resource Identifiers (URI) that link the data subject with a DID document. This document contains cryptographic material and secured by public-private key cryptography. A new identifier (DID) is then created from a cryptographic hash of the public key. A DID contains reference to the public key stored on the blockchain, which ensures identification of the identity holder (data subject) and the verifier. Singling out an entity or an individual is one of the key purposes of the public key: to guarantee that transactions are attributed to the correct entities. Hence, such identifier, along with the private key, qualifies as personal data (pseudonymized data per Article 4(5) and the GDPR (also see Recital 26 and 30 GDPR).
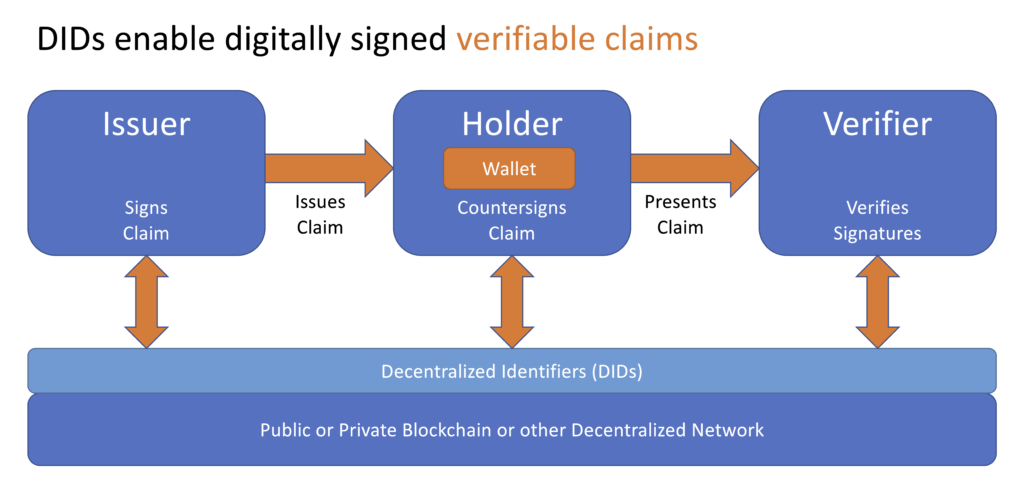
Verifiable Credentials
A verifiable credential is a set of tamper-proof claims and metadata that can show (cryptographically) the issuer. Credentials are the claims (statements) about the same data subject, e.g., the claim that Bilgesu is an alumni of Tilburg University. The most privacy-preserving feature of using DIDs in combination with VC is the possibility of partial (selective) disclosure of personal data. For example, if I want to buy alcohol from a supermarket, I can only show that over the threshold age for legally doing so.
A brief reality check
As acknowledged by the W3C Working Group, ‘privacy solutions are use case specific.’ For the alcohol buying scenario above, proof of age might not be enough to meet regulations and photo identification might still be required.
Moreover, the claims can be used together to indicate a set of information about an individual; they can be extended by adding additional claims., e.g., Bilgesu is an alumni of Tilburg University since 2020. Needless to say, when combined such personal data can be easily used to track and correlate a natural person.
These two points are not the only privacy considerations that should be taken into account when considering how much control and protection SSI systems provide. Device fingerprinting and usage patterns can be tracked by malicious actors because the networks are usually public and immutable. Moreover, the wallets might be vulnerable to cyberattacks such as phishing.
Consequently, SSI has attractive features that might reduce bulk data disclosures, eliminate certification authorities and the security risks stemming from their mediation. However, it does not provide a holy grail for data protection and more importantly, in the long run, it might not go further than providing a ‘feeling of control’ rather than a meaningful one.
Keywords: SSI, wallets, GDPR, DIDs, Verifiable Credentials
This blogpost was written by Bilgesu Sumer. Bilgesu has a bachelor’s degree in law and master’s degree in EU law from Marmara University. She has worked as a lawyer in the fields of corporate law and criminal law. She was awarded Jean Monnet Scholarship that sponsored her master’s degree in law and technology at Tilburg University, where she worked as a student assistant at cybersecurity project.