Digital Identity and Privacy – Where Are We Now
Abstract
Researchers have taken great efforts into the management of digital identities to ensure users’ privacy. This blog provides the examples where digitalization of services are applied and discusses the bottleneck and challenges of digital identity management.
Keywords: Self-Sovereign identity, Digital identity, Trust models
The digitalization of services today makes physical and digital worlds closely connected. For example, the power grid digitalization enables consumers to have better control over the physical system, the technology-enabled response center services ease the burden of clinical staff and help response center personnel to deliver homecare services to target patients efficiently, the digital socialization enables online interaction which brings people closer and helps them attract peer approval. With the interaction of the digital services, lots of digital identities emerge. An average data subject can obtain various identities associated with personal data at the same time, such as financial data, health data, governmental data, social data, etc. These digital identities with personal data, however, are faced with technological, legal, and operational challenges with data management and are in need of protection as well as physical identities. Many literatures mention these challenges including lack of standardized implementation methods to merge personal data with digital identity, security and privacy weakness in existing technologies, obsolete laws related to new disruptive technologies, universal understanding and acceptance of the users, difficulty in maintaining all identity repositories, etc. More precisely, in centralized and federated identity management systems, service providers provide users with identifiers and the stableness of the systems rely on users’ trust on these systems. The databases which store sensitive biometrics and biographical data in these systems are vulnerable in case of single point of failure. Once the user’s credential is disclosed, the attackers will have access to all the data of a user from other services. The loss of personal data will cause tremendous cost to stakeholders especially users.
What is put forward to help improve the management of digital identities?
To improve the management of these digital identities and provide users with a most trustful way, the “Self-Sovereign Identity” (SSI) architecture, which allows individuals rather than service providers to fully own, control, and manage their digital identity, is put forward by scholars. Allen defined ten principles of integration of SSI which includes existence, control, access, transparency, persistence, portability, interoperability, consent, minimization, and protection. A general understanding of SSI is that “it is intended to preserve the right for the selective disclosure of different aspects of one’s identity and the various components thereof, in different domains and contextual settings.”
Shifting the power from central authorities to entities, SSI is a user-centric approach relying on decentralized technology such as blockchain, cloud, and mobile computing technology. Instead of centralized authorities, the decentralized identity management where the core part is the SSI concept has helped eliminated the identity provider as third parties. As identifiers and associated personal data are securely stored by users, users will no longer acquire identity attributes from third parties or service providers. Consequently, it is believed that the security and privacy risks in third-party databases can be reduced, and data will be transferred in a more trustful way among different parties.
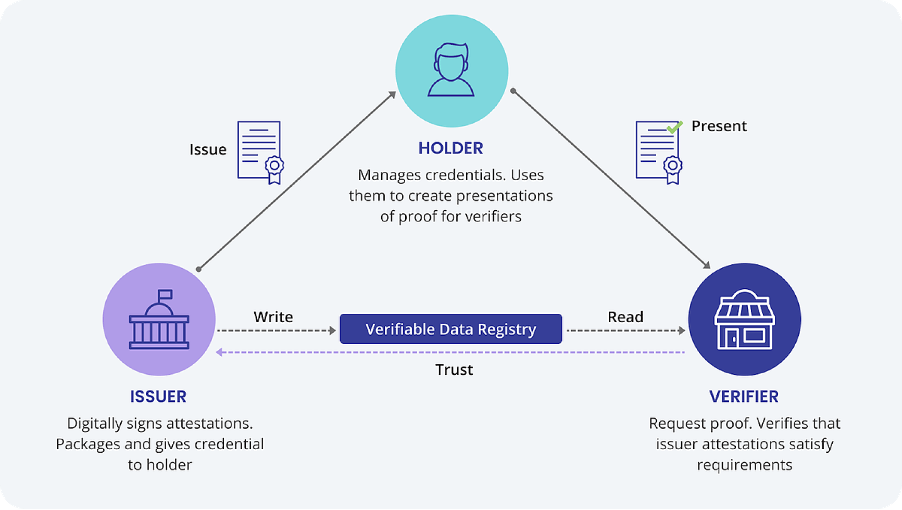
Fig. 1. Self-Sovereign Identity (SSI Safeguards Privacy by Removing the Need to Store Personal Information Entirely on a Central Database. (n.d.). https://cheqd.io/ssi/)
The bottlenecks and challenges of digital identity management
Even though the trust mechanism has been greatly changed in SSI, the new digital identity management systems are still faced with the bottlenecks and challenges like the lack of standards and regulations, lack of governance framework, or immaturity of the technology. Therefore, some researchers regard SSI as one step towards dealing with the aforementioned challenges instead of a mature solution. Trust assurance and privacy protection of the platforms and entities are one of the essential measures to improve SSI. To achieve it, a serious of technologies need to be applied in compliance with more standardized regulations, like trusted execution environments, secure multiparty computation and ring signature, threshold secret sharing, zero knowledge proofs, etc. On the other hand, as SSI is user-centric, different services and scenarios need to be identified and distinguished so that different stakeholders’ privacy can be taken into consideration at the same time. In certain cases, as users lose control of SSI, other parties must take over the control and help make decisions. It highly depends on laws and regulations adapted to privacy-respect and trust models of SSI.
Recommended resources:
- Islam, S. (2016). Digital applications in implementation of smart grid. In 2016 International Conference on Accessibility to Digital World (ICADW)(pp. 3-7). IEEE.
- Smith, J., Hewitt, B., & Skrbiš, Z. (2015). Digital socialization: Young people's changing value orientations towards Internet use between adolescence and early adulthood. Information, Communication & Society, 18(9), 1022–1038. https://doi.org/10.1080/1369118X.2015.1007074
- Shuaib, M., Alam, S., Alam, M. S., & Nasir, M. S. (2021). Self-sovereign identity for healthcare using blockchain.Materials Today: Proceedings.
- Reyna, A., Martín, C., Chen, J., Soler, E., & Díaz, M. (2018). On blockchain and its integration with IoT. Challenges and opportunities. Future generation computer systems, 88, 173-190.
- Wolfond, G. (2017). A blockchain ecosystem for digital identity: improving service delivery in Canada’s public and private sectors. Technology Innovation Management Review, 7(10).
- Preukschat, A., & Reed, D. (2021). Self-sovereign identity. Manning Publications.
This blogpost was written by Luyi Sun. Since 2020, she has been working in the eHealth and Welfare Security group in the Department of Information Security and Communication Technology, Norwegian University of Science and Technology, Norway. Her research topic is AI-based Privacy Agent towards Personalized Laws.